Featured Projects
DDOS attack detection and mitigation
OpenFlow SDN with Ryu Controller Integrated with Snort (Using GNS3 Environment)
DDOS attack detection and mitigation
Project IMage

Description
Objective
This project demonstrates the integration of OpenFlow SDN using the Ryu controller with Snort, a network intrusion detection system (NIDS), for mitigating Distributed Denial of Service (DDoS) attacks in a network environment. The project uses GNS3 to simulate the network topology and Ubuntu Server to host the Ryu controller and Snort NIDS. The goal is to showcase how SDN can dynamically detect and mitigate various types of network attacks, including ICMP, TCP, and UDP floods, using Ryu’s flow management and Snort’s attack detection capabilities.
Skills Learned
- Understanding of OpenFlow and SDN architecture.
- Configuring Ryu controller and integrating it with OpenFlow-enabled devices.
- Installing and configuring Snort as an Intrusion Detection System.
- Using GNS3 for creating and managing network simulations.
- Implementing dynamic network traffic control for DDoS mitigation.
- Working with network mirroring and monitoring traffic for attack detection.
Tools Used
- GNS3: For simulating the network topology with Cisco switches, routers, and virtual machines.
- Ryu Controller: For managing SDN flow tables and traffic routing.
- OpenvSwitch (OVS): For creating virtual switches and mirroring traffic to Snort.
- Snort: Network Intrusion Detection System (NIDS) used for detecting and alerting on DDoS attacks.
- Ubuntu Server: Hosting the Ryu controller, Snort, and other necessary components.
- Hping3: For simulating DDoS attacks in the network.
Steps
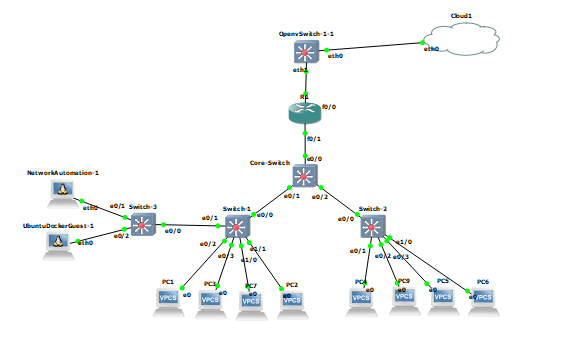
1. GNS3 Topology Setup
The GNS3 workspace was populated with the following devices:
- Four Cisco switches for the core network switches.
- One Cisco router for routing between networks.
- Ten host PCs connected to the switches for testing traffic generation.
- One OpenvSwitch (OVS) integrated into the topology to work with the Ryu controller.
- Ryu Controller running on an Ubuntu server, responsible for managing traffic and flows.
- Snort IDS installed on the Ubuntu server to monitor and analyze network traffic.
2. Configuring OpenvSwitch (OVS)
OpenvSwitch (OVS) was installed on the Ubuntu server and configured to act as the central switch in the SDN network. To enable OVS and establish communication with the Ryu controller, the following commands were used:
# Install OVS sudo apt install openvswitch-switch
# Start OVS service sudo service openvswitch-switch start
# Create a bridge and add the interface sudo ovs-vsctl add-br br0 sudo ovs-vsctl add-port br0 eth0
# Set up traffic mirroring for Snort ovs-vsctl -- --id=@p get port br0 -- --id=@mirror create mirror name=snort-mirror select-all=true output-port=@p -- -- set Bridge br0 mirrors=@mirror
# Link OVS to the Ryu controller sudo ovs-vsctl set-controller br0 tcp:192.168.234.236:6633
3. Ryu Controller Setup
Ryu was installed on the Ubuntu server using the following commands:
# Install necessary packages sudo apt update sudo apt install python3 python3-pip xterm iperf hping3 net-tools wireshark apache2-utils curl
# Install Ryu sudo pip3 install ryu
# Verify installation ryu-manager --version
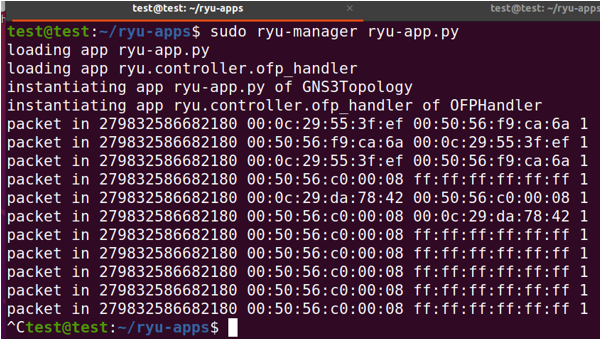
# Run Ryu application ryu-manager ryu-app.py
4. Snort Installation and Configuration
Snort was installed and configured as follows:
# Install Snort sudo apt-get update sudo apt-get install snort
# Configure Snort to monitor traffic sudo snort -A console -c /etc/snort/snort.conf -i eth0
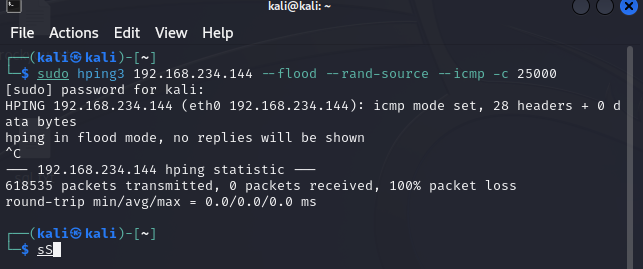
5. DDoS Attack Simulation with Hping3
To simulate DDoS attacks, the following commands were used:
ICMP Flood
hping3 --icmp --flood --rand-source <destination_ip>
TCP Flood
hping3 --flood -S --rand-source -p 80 <destination_ip>
UDP Flood
hping3 --udp --flood --rand-source -p 161 <destination_ip>
6. Integration of Ryu and Snort for DDoS Mitigation
- Network Setup: Ryu controller and Snort are configured to work together on the same server.
- Traffic Mirroring: OVS mirrors all network traffic to Snort for inspection.
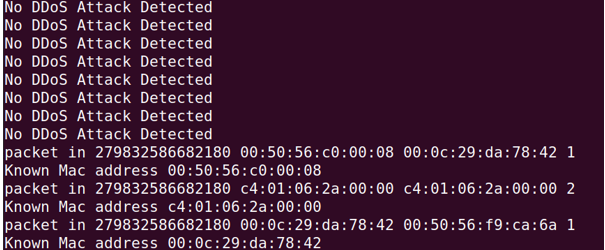
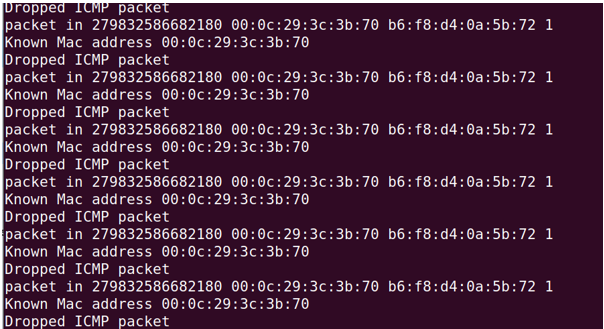
- Attack Detection: Snort analyzes the incoming traffic for known attack patterns (ICMP, TCP, UDP floods).
- Alert Generation: Upon detection, Snort generates an alert and sends it to the Ryu controller.
- Dynamic Flow Modification: Ryu receives the alert and modifies the network flow table to mitigate the attack by blocking or rerouting malicious packets.
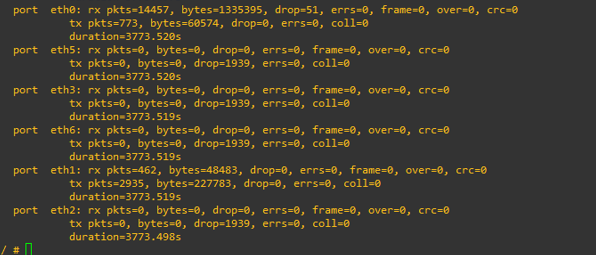
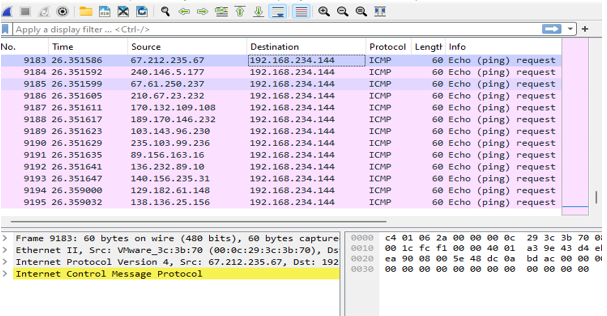
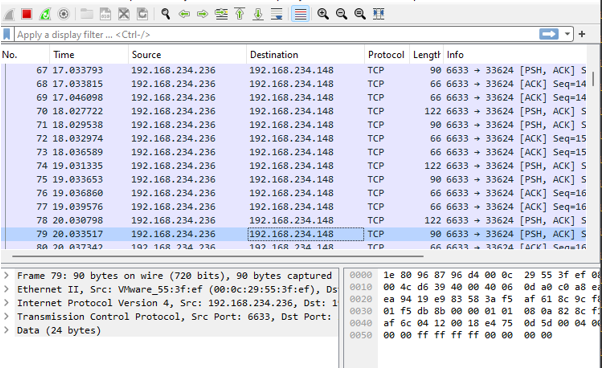
7. Experiment Results
Various types of DDoS attacks were simulated. The integration of Snort and Ryu provided an effective mitigation strategy. Dynamic flow control enabled the SDN network to detect and block malicious traffic in real-time, ensuring the availability and security of the network.
Conclusion
This project showcases how OpenFlow SDN and Ryu controller, when integrated with Snort IDS, can effectively mitigate DDoS attacks. By dynamically adjusting traffic flows based on attack detection, the system can prevent network disruptions and maintain service continuity.
For any questions or further assistance for the python code, please contact me - 📧 Email: johnusiabulu@cipherknights.com .
Wireshark analysis in the network during DDOS attacks.
Wireshark analysis in the network after DDOS attacks mitigated.
Technologies Used
Ryu Controller GNS3 Snort OPenflow Wireshark
Computer-Forensic-Investigation-Project.
This project is a fictional case created for demonstration purposes. It is not related to any real-…
Computer-Forensic-Investigation-Project.
Project IMage


Description
Objective
The objective of this forensic investigation was to thoroughly examine digital evidence related to a criminal activity involving arson and fraud. The investigation focused on acquiring and analyzing data from multiple sources, including mobile phones, solid-state drives (SSDs), and USB sticks. This case aimed to uncover evidence that could help establish the involvement of individuals in planning and executing a fire at a storage facility, resulting in a fatality and an insurance fraud scheme.
This investigation was conducted in strict compliance with the Association of Chief Police Officers (ACPO) guidelines, ensuring proper evidence handling and integrity throughout the process.
Skills Learned
- Forensic Data Acquisition: Gained hands-on experience in acquiring data from various digital devices using industry-standard forensic tools.
- Digital Evidence Analysis: Developed proficiency in using forensic tools like FTK Imager and Autopsy to analyze file structures, recover deleted files, and identify crucial digital evidence.
- Password Cracking: Enhanced skills in password recovery techniques using tools like John the Ripper to decrypt encrypted files.
- Cryptographic Analysis: Applied knowledge of encryption and hashing algorithms to validate the integrity of evidence and uncover hidden data.
- Chain of Custody Management: Gained experience in maintaining the integrity of evidence by following strict procedures for data acquisition and handling.
Tools Used
- FTK Imager: A tool used for creating bit-for-bit forensic images of storage devices.
- Autopsy: Open-source software for analyzing forensic images, recovering deleted files, and examining file metadata.
- John the Ripper: A password cracking tool used to decrypt encrypted Word documents.
- Write Blocker: A hardware tool used to prevent accidental modification of evidence during the acquisition process.
- Kali Linux: A Linux distribution used for forensic investigations, particularly for running John the Ripper.
Steps
1. Crime Scene Visit
Objective: To secure the crime scene, identify potential evidence, and document the environment for analysis while adhering to ACPO guidelines.
-
Documenting the Scene:
- Photographed and recorded the layout of the crime scene, focusing on areas of interest, including the storage facility, suspect's workstation, and any devices or storage media found.
- Collected physical evidence, including mobile phones, an SSD, a USB stick, and handwritten notes, following strict evidence handling protocols.
-
Tagging Evidence:
- Each piece of evidence was assigned a unique identifier and placed in evidence bags with tamper-proof seals.
- A detailed log was created, noting the date, time, location, and description of each item collected.
-
Transporting Evidence:
- The collected evidence was securely transported to the forensic lab while maintaining a proper chain of custody to prevent contamination or tampering.
2. Data Acquisition
Objective: To acquire data from the SSD and USB stick while ensuring data integrity using FTK Imager and write blockers.
-
Acquiring Data from the SSD:
- Attached the SSD to the write blocker to prevent data modification during the acquisition.
- Connected the SSD to the computer and used FTK Imager to create a bit-for-bit image of the drive.
- The forensic image was saved in the E01 format and hash values (MD5, SHA-1) were generated to verify data integrity.
-
Acquiring Data from the USB Stick:
- Similar procedure was followed for the USB stick using FTK Imager.
- A forensic image of the USB drive was created and stored in a separate folder with appropriate hash values to verify its integrity.
3. Data Analysis
Objective: To analyze the forensic images from the SSD and USB stick using Autopsy and recover relevant evidence.
-
Loading Forensic Images into Autopsy:
- Opened Autopsy on the analysis workstation and created a new case for the investigation.
- Added the forensic image files (E01) of the SSD and USB stick as data sources in Autopsy.
-
Examination of SSD Files:
- After ingestion, Autopsy was used to browse the file system on the SSD. I found several relevant files in the "Bad Items" folder.
- Notably, Word documents named Skype.exe, Order.docx, Task.docx, and Rob.docx were discovered, all of which were encrypted with passwords.
-
Examination of USB Stick Files:
- Similar analysis was conducted on the USB stick, where encrypted documents were found in the "Bad Items" folder.
- These documents contained valuable evidence linking the suspects to the crime, including plans to carry out the arson.
4. Decrypting Encrypted Files
Objective: To decrypt the encrypted Word documents found on the SSD and USB drive.
-
Using John the Ripper for Password Cracking:
- The encrypted Word documents (Skype.exe, Order.docx, Task.docx, Rob.docx) were extracted and stored in a folder on Kali Linux.
- John the Ripper was set up on a Kali Linux virtual machine to perform brute-force password cracking on the documents.
-
Cracking the Passwords:
- Using a wordlist (rockyou.txt), John the Ripper attempted to brute-force the passwords for the encrypted documents.
- The process revealed the passwords, allowing access to the content of the documents, which contained critical communications and instructions for executing the crime.
5. Investigating Evidence
Objective: To analyze the decrypted documents and identify key evidence linking the suspects to the crime.
-
Content Analysis of Rob.docx:
- The document revealed instructions to turn off safety measures and spill fuel in the storage facility, which was part of the plan to set it on fire.
-
Corroborating Evidence from the SSD:
- The analysis of the SSD's email folder revealed communication between the suspects, confirming the planning of the arson and fraud.
6. Reporting and Chain of Custody
Objective: To compile findings into a forensic report while ensuring the integrity of the evidence.
- Creating the Final Report:
- A detailed forensic report was generated, summarizing the findings from the SSD, USB stick, and decrypted documents.
- All evidence was securely stored, and the chain of custody was meticulously documented to ensure the integrity of the evidence.
Conclusion
This forensic investigation successfully uncovered crucial evidence linking the suspects to the arson and fraud scheme. The skills and tools learned during this project can be applied to similar investigations and are valuable for anyone pursuing a career in digital forensics.
Technologies Used
FTK Tool FTK Imager Autopsy Write Blocker John The Ripper
Prousse Fashion
E-Commerce Website for African Traditional Clothing
Prousse Fashion
Project IMage

Description
Client: Prousse Fashion
Location: United Kingdom
Industry: Fashion / E-Commerce
Prousse Fashion is a UK-based company specializing in African traditional clothing. They needed a modern, user-friendly e-commerce platform to connect with a global audience and showcase their vibrant, culturally rich fashion line.
I designed and developed a fully responsive e-commerce website tailored to their brand, offering a seamless and intuitive shopping experience. The site includes dynamic product listings, secure payment integration, and mobile optimization to ensure accessibility for all users.
In addition to development, I implemented SEO best practices to optimize the site for niche keywords related to African fashion. This resulted in increased search visibility, more organic traffic, and a stronger presence in a highly competitive market.
Key Highlights:
-
Custom-built e-commerce platform with an easy-to-manage product inventory
-
Mobile-friendly design, ensuring accessibility across all devices
-
SEO optimization targeting African fashion keywords
-
Improved organic search rankings and increased online visibility
-
Ongoing maintenance and updates for security and inventory management
This project helped elevate Prousse Fashion’s online presence, drive sales, and build brand recognition on a global scale.
Technologies Used
Django JS CSS HTML
UVC Legal
Immigration Law Website Design & SEO
UVC Legal
Project IMage

Description
Client: UVC Legal
Location: United Kingdom
Industry: Legal Services / Immigration
UVC Legal is a trusted immigration advisory firm providing expert legal support for visa and employment-related matters. They needed a professional, user-friendly website to represent their services and build trust with clients navigating complex immigration processes.
I designed and developed a clean, responsive website that clearly communicates UVC Legal’s expertise and services. The layout and structure were carefully crafted to make it easy for potential clients to find the information they need and get in touch.
To increase online visibility, I implemented an SEO strategy targeting high-volume legal terms related to immigration and employment. This helped UVC Legal rank higher in search engine results, drawing in more traffic and qualified leads.
Key Highlights:
-
Professionally designed website with clear service presentation
-
Responsive, mobile-friendly layout for better user experience
-
SEO optimization targeting immigration and visa-related keywords
-
Improved search rankings and increased client inquiries
-
Ongoing updates to reflect legal changes and evolving client needs
This project positioned UVC Legal as a credible authority in immigration law and helped them expand their client base through a stronger online presence.
Technologies Used
Django JS CSS HTML
Peasiso Care Services
Peasiso Care Services is a UK-based care agency providing high-quality domiciliary care and staffin…
Peasiso Care Services
Project IMage

Description
They needed a professional and easy-to-navigate web platform that would clearly communicate their services, attract care workers, and support agency operations.
I designed and developed a fully responsive web application that serves both as an information hub for care services and a recruitment portal for healthcare professionals. The site highlights Peasiso’s commitment to compassionate care while also offering a streamlined process for prospective staff to apply online.
This solution enhances their digital presence, improves client trust, and helps automate parts of the hiring and onboarding process.
Key Highlights:
-
Custom-built care services web app with clear service offerings and agency capabilities
-
Job application and staffing portal for care professionals seeking work opportunities
-
Mobile-optimized design for accessibility and ease of use on all devices
-
SEO implementation to improve visibility in healthcare and staffing-related searches
-
Secure contact and application forms for client inquiries and staff recruitment
-
Ongoing updates and support for functionality, performance, and compliance
The new platform has strengthened Peasiso Care Services’ credibility, streamlined staff recruitment, and positioned them as a reliable partner for both clients and caregivers in the UK care sector.
Technologies Used
Django JS CSS HTML
Toraja Spring Care Home
Website Design & Local SEO
Toraja Spring Care Home
Project IMage

Description
Client: Toraja Spring Care Home
Location: United Kingdom
Industry: Health & Social Care
Toraja Spring Care Home offers professional and compassionate elderly care in the UK. They needed a modern, informative website to better communicate their services and connect with families looking for trusted care options.
I designed and developed a clean, user-friendly website that’s easy to navigate and accessible across all devices. My focus was on creating a welcoming digital space that reflects the warmth and reliability of the care they provide.
To help them reach more local families, I implemented tailored local SEO strategies, optimizing the website for elderly care-related search terms within their region. This improved their visibility in local search results, leading to a noticeable increase in client inquiries.
What I Delivered:
-
Custom-built website with intuitive navigation
-
Responsive design for all devices
-
Local SEO optimization targeting care-related searches
-
Clear service information and strong calls to action
-
Ongoing support to keep the site updated and compliant
This project helped Toraja Spring strengthen their online presence, build trust with potential clients, and increase engagement with families seeking quality care services.
Technologies Used
Django JS CSS HTML
JiT Accountants
JIT Accounting is a UK-based accounting firm offering expert financial and tax services for individ…
JiT Accountants
Project IMage





Description
To support their digital transformation and improve client engagement, I designed and developed a custom accounting web application tailored to their business model.
The platform features a free tax calculator tool that allows users to quickly estimate their taxes—no registration required. For users who wish to go further, the app provides a seamless onboarding system that unlocks access to a powerful, client-friendly accounting software suite upon registration.
This solution not only simplifies the accounting process for clients but also enhances JIT Accounting's ability to attract, engage, and convert site visitors into loyal customers.
Key Highlights:
-
Custom-built accounting web app with intuitive user interface and user journey
-
Free tax calculator tool to drive organic engagement and provide immediate value
-
Secure registration system to unlock full accounting software features
-
Mobile-optimized design ensuring usability across all devices
-
SEO-friendly development to boost visibility in searches related to UK tax services
-
Ongoing maintenance to support security, feature enhancements, and performance
This project positioned JIT Accounting as a forward-thinking, tech-enabled service provider, helping them reach a broader audience and deliver real-time financial tools to clients at every stage of their journey.
Technologies Used
Django JS CSS HTML
Yout Express Services
Car Hire & Drop-off Booking Platform
Yout Express Services
Project IMage

Description
Client: You Express Services
Location: United Kingdom
Industry: Transportation / Car Hire
You Express Services is a UK-based company offering convenient car hire and drop-off services. They needed a reliable online platform to streamline bookings and improve customer experience.
I designed and developed a seamless, user-friendly website that allows customers to easily book car hire and drop-off services. The platform is fully responsive and optimized for speed and usability, making it simple for users to navigate and complete their bookings from any device.
To help boost their online presence, I implemented tailored local SEO strategies targeting car hire and transportation keywords specific to their service areas. This significantly improved their visibility in search engine results, attracting more local traffic and increasing client inquiries.
Key Highlights:
-
Custom booking platform designed for ease of use
-
Fully responsive and mobile-optimized interface
-
Local SEO implementation for increased visibility in targeted regions
-
Enhanced user experience leading to higher customer satisfaction
-
Ongoing website support, including security, performance, and updates
This project helped You Express Services grow their online reach, improve customer engagement, and drive more business through their digital platform.
Technologies Used
Django JS CSS HTML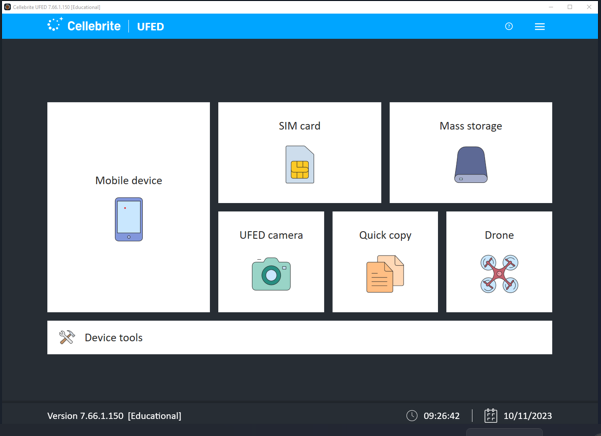
Mobile Phone Forensics Investigation
IMPORTANT: THIS PROJECT IS NOT FOR EDUCATIONAL PURPOSES AND DOES NOT REPRESENT A REAL CASE.
Mobile Phone Forensics Investigation
Project IMage

Description
This project simulates a mobile phone forensics investigation and is intended purely for demonstration, practice, or research purposes in a controlled environment. Any resemblance to actual persons, living or dead, or actual events is purely coincidental. The data, tools, processes, and findings presented here are entirely fictional, and no real-world legal or ethical implications should be inferred from this simulation.
Key Points:
- Not for Educational Use: This project is not intended as a teaching resource or educational material. It is designed to simulate an investigative process for the purpose of practice and skill development.
- Fictional Data and Case: All data used in this simulation, including but not limited to device data, user profiles, and communication logs, are fabricated and do not reflect any real-world individual or event.
- Not a Real Investigation: The processes, tools, and methodologies shown are for illustrative purposes only and are not meant to replicate actual forensic investigation procedures used in real cases.
- Ethical Use: The tools and methods demonstrated should only be used in compliance with legal and ethical standards, and only by authorized personnel in legitimate investigative contexts.
Project Overview
This project simulates a forensic investigation of a mobile phone to demonstrate the process of extracting and analyzing digital evidence. The primary focus is on mobile device forensics, the use of forensics tools like Cellebrite, and the examination of user data such as messages, call logs, photos, and more.
Objective
The objective of this project is to showcase how forensic investigators can extract, analyze, and present data from a mobile device in a simulated investigation. Key areas covered include:
- Extraction of mobile device data using forensic tools.
- Analysis of digital evidence from the mobile device.
- Creation of a detailed report based on the findings.
- Presentation of evidence that can be used in a simulated legal scenario.
Tools Used
- Cellebrite UFED: A tool used for extracting data from mobile devices.
- Cellebrite Analyzer: A tool for analyzing and interpreting extracted mobile data.
- iPhone 6s: A test mobile device used in this project (fictional data).
Skills Learned
- Understanding the process of mobile device data extraction.
- Analyzing digital evidence from mobile devices.
- Utilizing forensic software tools such as Cellebrite UFED and Analyzer.
- Creating detailed forensic reports based on the evidence found.
Steps
1. Mobile Device Identification and Data Extraction
In this step, the mobile device was identified and connected to the forensic tool (Cellebrite UFED). The tool extracted data including call logs, text messages, and multimedia files.
The device’s operating system, model, and serial number were captured for documentation.
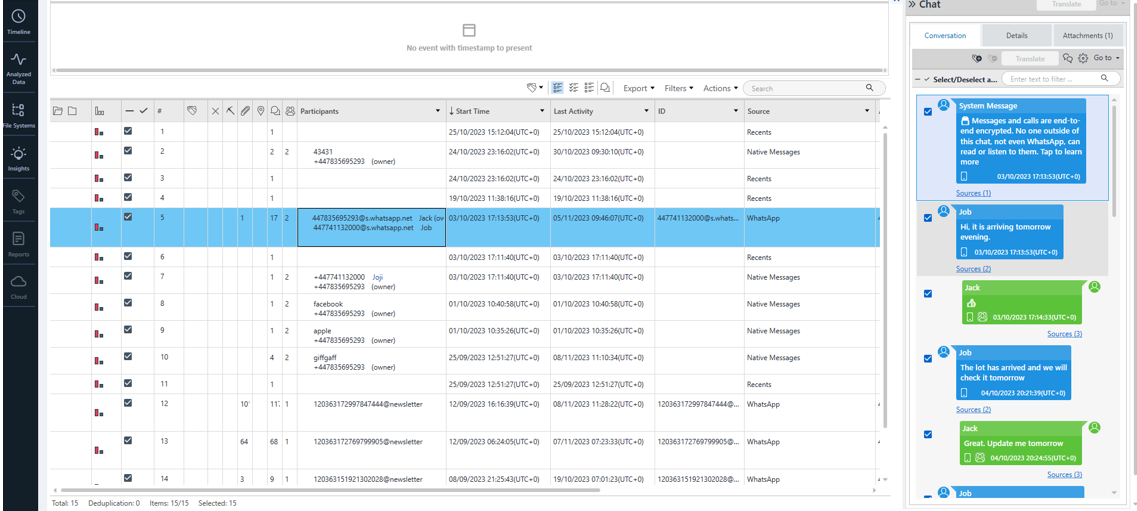
The extraction process captured data from various app sources, including SMS, WhatsApp, and photos.
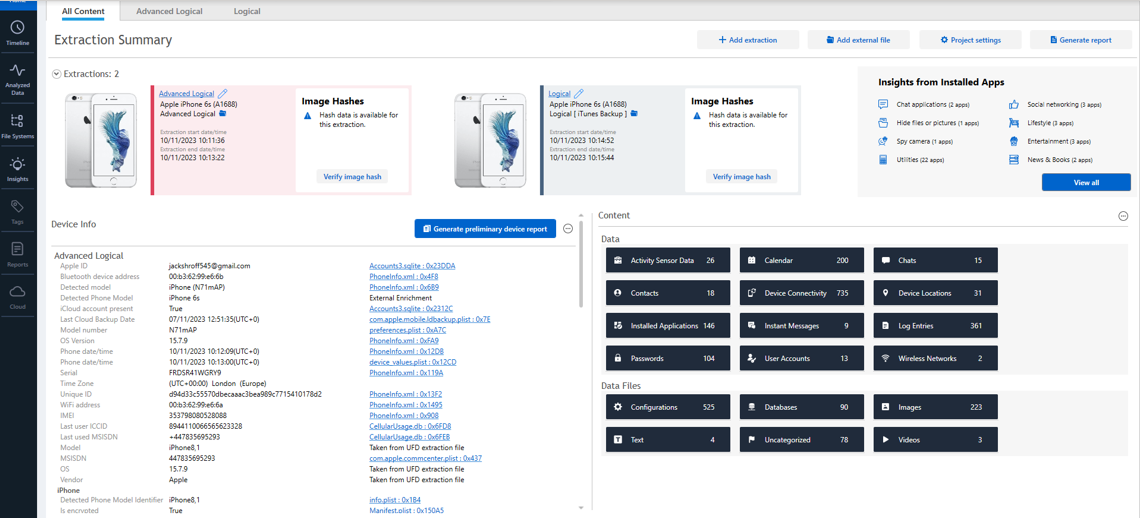
2. Data Analysis Using Cellebrite Analyzer
After the data was successfully extracted, it was imported into Cellebrite Analyzer for further examination. In this stage, we identified key pieces of evidence such as chat logs and timestamps.
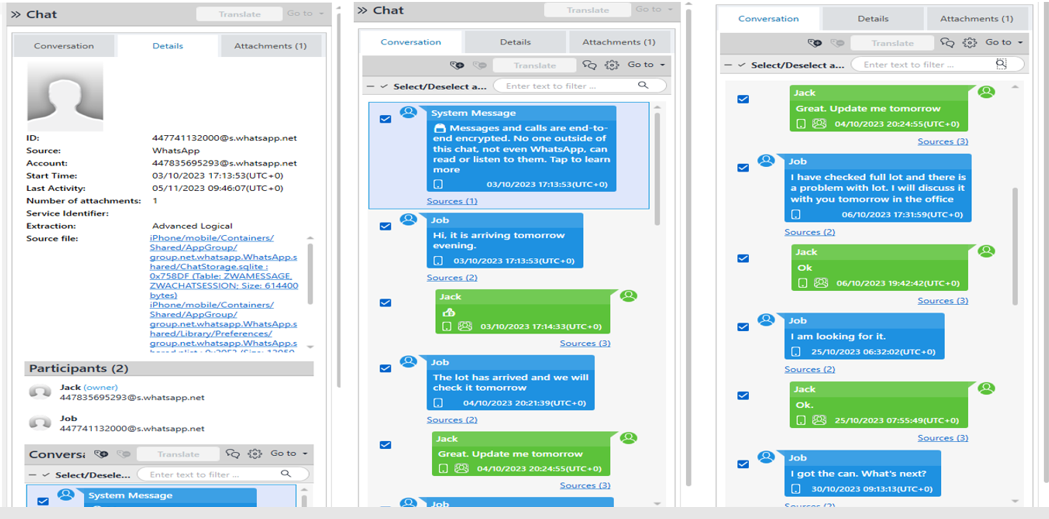
Here, you can see the data from WhatsApp chat logs and photos being imported and parsed.
The analyzer provides a detailed view of the extracted messages, contacts, and multimedia files.
3. Expert Opinion and Findings
The forensic analysis revealed several important findings, including the identification of specific communication patterns that could indicate criminal activity. The metadata analysis of the photos also revealed timestamps that were crucial to the investigation.
This document contains a summary of the expert’s analysis and the significance of the findings.
4. Reporting and Documentation
The final step involved compiling all findings into a detailed report, summarizing the methods used, evidence collected, and the conclusions drawn from the analysis.
The report includes an executive summary, the methodology used, and a detailed description of all extracted data and findings.
Conclusion
This project demonstrates the key stages of a mobile phone forensic investigation, from data extraction to analysis and reporting. While this project is entirely fictional and for demonstration purposes, it showcases the capabilities of forensic tools and the importance of proper documentation and ethical practices in real forensic investigations.
Important Note
- Fictional Data: All the data used in this project, including text messages, photos, and call logs, are fabricated and do not belong to any real individual.
- No Real-Life Application: This project does not represent an actual criminal investigation. The processes and findings are used solely to illustrate the capabilities of forensic tools and techniques in a controlled, simulated environment.
- Ethical Guidelines: In real-world forensic investigations, it is crucial to follow all legal and ethical guidelines. This includes obtaining proper consent, following the law, and maintaining the privacy and security of all involved parties.
Legal Disclaimer
This project is for demonstration purposes only and does not involve real individuals, real data, or real-world legal proceedings. Any use of forensic tools and methods should only be done by certified professionals and in accordance with applicable laws and ethical standards.
Technologies Used
Cellebrite UFED
Church Of Salvation Okeigbala
Church, Community-Focused Website Design
Church Of Salvation Okeigbala
Project IMage

Description
Client: Church Of Salvation Okeigbala
Location: United Kingdom
Industry: Faith / Community
Church Of Salvation Okeigbala needed a welcoming and informative website to help them connect with their congregation and reach new members in their community. Their goal was to create an online space where people could easily access church information, stay updated on events, and engage more deeply with their faith.
I designed and developed a responsive, easy-to-navigate website that reflects the spirit and mission of the church. The platform allows visitors to view sermons, get event updates, and make online donations—all with a few simple clicks.
To improve discoverability, I implemented local SEO strategies to ensure the church ranks well for searches related to faith communities in their area. This helped boost their visibility online and made it easier for people to find and connect with them.
Key Highlights:
-
Clean, accessible website tailored for community engagement
-
Integration of sermon uploads, events calendar, and online giving
-
Local SEO implementation to increase visibility in regional search results
-
Increased engagement and easier access for church members
-
Ongoing support and updates to keep content fresh and the site fully functional
This project helped Church Of Salvation Okeigbala strengthen their digital presence and better serve their growing community both online and offline.
Technologies Used
Django JS CSS HTML
Opulenta Suites
Luxury Airbnb Booking Platform
Opulenta Suites
Project IMage




Description
Client: Opulenta Suites
Location: United Kingdom
Industry: Hospitality / Short-Term Rentals
Opulenta Suites offers high-end, short-term rental accommodations and needed a polished, user-friendly website to support direct bookings and enhance their brand presence. Their goal was to simplify the booking experience while appealing to a clientele looking for luxury stays.
I designed and developed a sleek, fully responsive booking platform that allows guests to easily browse listings, view amenities, and reserve accommodations directly from the site. The design reflects the premium feel of the brand while ensuring ease of use across all devices.
To drive more visibility, I implemented an SEO strategy focused on luxury short-term rental keywords, which helped improve the site’s rankings and increase organic traffic.
Key Highlights:
-
Custom booking platform tailored for luxury short-term rentals
-
Seamless user experience with a mobile-first design
-
SEO optimization targeting luxury travel and Airbnb-style keywords
-
Streamlined booking process that boosted conversions
-
Ongoing maintenance to ensure smooth performance and updates
This project elevated Opulenta Suites’ online presence, attracted more qualified leads, and provided guests with a convenient way to book premium stays.
Technologies Used
Django JS CSS HTML
HICMK Cleaning Services
Website Design & SEO for Cleaning Company
HICMK Cleaning Services
Project IMage

Description
Client: HICMK Cleaning Services
Location: United Kingdom
Industry: Cleaning / Residential & Commercial Services
HICMK Cleaning Services is a trusted provider of residential and commercial cleaning solutions. They needed a professional and user-friendly website that clearly communicated their services and made it easy for customers to book appointments online.
I designed and developed a sleek, responsive website that showcases their service offerings, transparent pricing, and real customer testimonials. The platform includes a streamlined booking system, allowing clients to quickly schedule cleaning services with minimal hassle.
To attract more organic traffic, I built out detailed service pages and integrated an SEO-optimized blog targeting key phrases related to cleaning services, deep cleaning, and office sanitation. I also added a contact form and inquiry system to simplify communication and improve lead generation.
Key Highlights:
-
Clean, responsive design tailored for service-based businesses
-
Intuitive online booking system for residential and commercial cleaning
-
SEO-focused content and blog to drive organic traffic
-
Integrated contact and inquiry forms for better customer engagement
-
Ongoing maintenance including updates, security, and SEO performance
This project helped position HICMK Cleaning Services as a reliable and accessible cleaning company, boosting their online visibility and increasing conversions through a modern, efficient digital platform.
Technologies Used
Django JS CSS HTML
KDK Cleaning Services
KDK Cleaning Service is a UK-based company offering a wide range of professional cleaning services …
KDK Cleaning Services
Project IMage



Description
They approached me to create a modern, trustworthy, and user-friendly website that reflects their high standards and reliability in the cleaning industry.
I designed and developed a fully responsive website that showcases their wide array of cleaning services, from regular domestic cleaning to deep commercial cleans. The site includes clear service descriptions, customer testimonials, and an easy-to-use contact form to encourage inquiries and bookings.
This digital presence not only builds trust with potential customers but also streamlines client engagement and supports the growth of KDK’s brand across the UK.
Key Highlights:
-
Custom-developed service website tailored to KDK’s brand and offerings
-
Mobile-friendly design for a smooth experience on all devices
-
Clear service breakdowns to help users find the right solution quickly
-
Integrated contact and quote request forms for lead generation
-
SEO optimization to improve visibility for cleaning-related keywords
-
Ongoing support for updates, speed, and security
The new website has helped KDK Cleaning Service build credibility, attract new clients, and improve communication with both residential and commercial customers.
Technologies Used
Django JS CSS HTMLUVC Transport
UVC Transport is a UK-based vehicle hire company offering reliable and flexible transport solutions…
UVC Transport
Description
They needed a modern, functional website to establish their online presence, highlight their fleet, and make it easy for customers to book or inquire about vehicle hire services.
I designed and developed a clean, responsive website that effectively showcases UVC Transport’s services, vehicle options, and commitment to customer satisfaction. The platform includes key features such as service overviews, vehicle listings, and a user-friendly contact and booking form to streamline the customer journey.
This website now serves as a vital tool for UVC Transport, helping them build trust, attract new clients, and compete effectively in the vehicle hire industry.
Key Highlights:
-
Custom-designed vehicle hire website reflecting UVC Transport’s brand and offerings
-
Fully responsive layout for optimal experience on desktop, tablet, and mobile
-
Service and fleet showcase to clearly communicate options and availability
-
Integrated contact/booking forms to drive conversions and inquiries
-
SEO optimization targeting vehicle hire and transport keywords
-
Ongoing maintenance for performance, security, and content updates
This project has equipped UVC Transport with a strong digital presence, making it easier for customers to find and engage with their services across the UK.